TLDR;
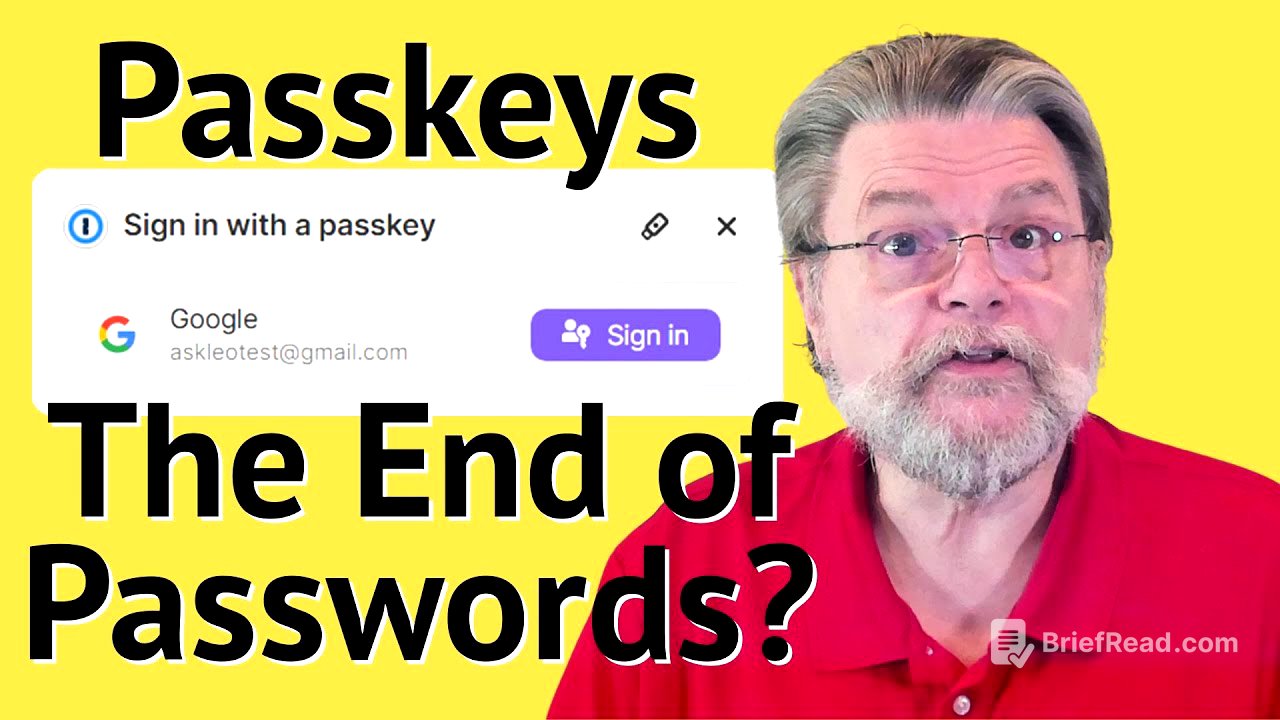
This video explains what passkeys are and how they differ from passwords and passphrases. It covers the underlying technology of public key cryptography, how passkeys are set up and used, their security advantages, and where they are stored. The key takeaway is that passkeys are a more secure and user-friendly authentication method that is gradually replacing passwords.
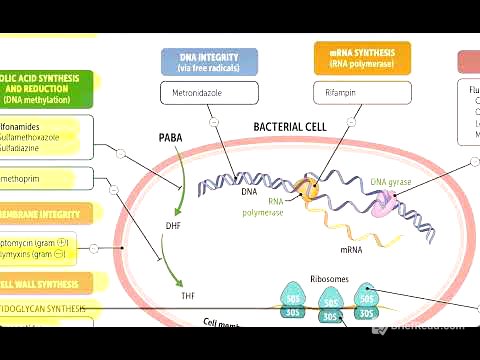
- Passkeys use public key cryptography for secure authentication.
- They are unique to each device and service, enhancing security.
- Passkeys are more resistant to phishing, data breaches, and keyloggers compared to passwords.
What Is a Passkey? [0:00]
The video introduces passkeys as a new authentication method designed to replace the traditional password. Passkeys aim to simplify the login process by securely and automatically signing users into their devices and accounts. The presenter differentiates passkeys from passwords, which are character-based, and passphrases, which are multiple words. Passkeys utilize public key cryptography, offering enhanced security and ease of use, although the underlying technology is complex.
What is a passwords [0:45]
Passwords are an authentication method where users verify their identity by entering a pre-defined sequence of characters. The strength of a password depends on its length, complexity, and unpredictability. Short and simple passwords like "password" are easily compromised, while long, random passwords are more secure.
Passphrases [1:25]
Passphrases consist of multiple words and offer an alternative to complex passwords. A good passphrase should be lengthy and composed of unrelated words to avoid being easily guessed. Examples include "correct horse battery staple," which was effective until its widespread use as an example.
Key pairs [2:35]
Public key cryptography relies on creating two large numbers, A and B, using a special mathematical formula. These numbers have a unique relationship: one cannot be calculated from the other, and data encrypted with one key can only be decrypted with the other. If data is encrypted using key A, only key B can decrypt it, and vice versa.
Public and private [4:10]
In public key cryptography, one key is designated as the public key, while the other is kept secret as the private key. If key A is kept secret and key B is made public, anyone can encrypt data using the public key B, but only the owner of the private key A can decrypt it. Conversely, if the owner encrypts data using their private key A, anyone can verify that only they could have encrypted it by decrypting it with the public key B.
Public key authentication [5:15]
Public key encryption enables passwordless authentication, a method used on Linux systems for decades. A user creates a key pair, keeps the private key secure, and provides the public key to the server they want to access. When the user tries to log in, the server encrypts a number using the public key and sends the encrypted result to the user. The user's system decrypts the number using the private key and responds with the correct number, proving their identity without a password.
Passkeys and public key authentication [6:40]
Passkeys are public-private key pairs automatically generated for users. The public key is stored on the service supporting passkeys, while the private key is securely stored on the user's device. During sign-in, the service sends a challenge encrypted with the public key, which the user's device decrypts using the private key, granting access.
Passkeys are unique to each device [7:25]
Passkeys are unique to each device, meaning a different key pair is generated for each device used to access an account. For example, a user might have separate key pairs for their Google account on their desktop, laptop, and phone. This is managed behind the scenes, with the service tracking all public keys associated with the account and each device storing the private keys for the accounts set up on that device.
Passkey setup [8:20]
Setting up passkeys varies depending on whether you're creating a new account or adding a passkey to an existing account on a new device. When creating a new account, the setup process generates the key pair and stores the private key on your device. Users should also set up alternative authentication methods like email or mobile number for signing in on devices without a passkey. When signing into a new device, users first authenticate using an alternative method, then set up a passkey for future logins.
Using passkeys [11:05]
To sign in with a passkey, users unlock their device using a PIN, facial recognition, or fingerprint. This action grants access to the account. Even if the device is already unlocked, using a passkey requires re-authentication to prevent unauthorized access. While alternative sign-in methods exist, they are more cumbersome, involving codes sent via email or text, or notifications on other devices.
Passkeys and two-factor authentication [12:30]
Passkeys are often confused with two-factor authentication, but they are distinct. Passkeys replace passwords, while two-factor authentication adds an extra layer of security. When signing into a new device with two-factor authentication enabled, users may need to complete the two-factor authentication process before setting up a passkey for streamlined future logins.
Why passkeys are secure [13:20]
Passkeys offer enhanced security compared to passwords, protecting against common threats like data breaches, phishing, malware, and brute force attacks. In a data breach, the public key is useless to attackers. Passkeys cannot be phished or captured by keyloggers. If a device is lost, passkeys are protected by the device's unlock process and can be revoked remotely. Additionally, passkeys eliminate the risk of password reuse, as they are unique to each device and account.
Where passkeys are stored [16:00]
Passkeys are stored securely in several ways: the operating system's secure credential storage (like Windows Hello), password managers, or hardware security keys. Storing passkeys in the operating system's secure storage is the default method, requiring a PIN, face, or fingerprint for access. Password managers allow users to use the same passkey on multiple devices. Hardware security keys, like YubiKeys, can store a limited number of passkeys for portable security.

![16년차 앱등이가 갤럭시로 넘어가려는 이유 [갤럭시 Z 폴드7 리뷰]](https://wm-img.halpindev.com/p-briefread_c-10_b-10/urlb/aHR0cDovL2ltZy55b3V0dWJlLmNvbS92aS9hQmRCcmVuNFRpZy9ocWRlZmF1bHQuanBn.jpg)